First run a full scan against your home IP address. Advanced IP Scanner is one of the programs that undoubtedly supports this fundamental step of Network PenTesting.
It is free compatible with Windows 10 and does not require complicated installation and use processes.

. The first thing they are going to do is port scan your IP address and find out what youve got running if anything. To do this open a port on your router and rerun the scan. Discovery After your organization has developed a strategy for the network pentest its time to initiate reconnaissance.
First run a full scan against your home IP address. In case you have a trusted external pen testing tool and you know the public IP then you can try allowing traffic from that IP to the internal test network for pen testing. Ii Configure the exploit with remote IP address and remote port number.
Wi-Fi can be connected to Kali Linux using the following steps. Advanced IP Scanner is one of the programs that undoubtedly supports this fundamental step of Network PenTesting. Overall if youre opening one port for the game server on your firewall then all the testing and vuln scanners will tell you nothing.
Hacking into other peoples computers and networks is illegal without prior consent but its perfectly legal to set up your own lab that mimics someone elses environment and then pentest your copy. Iv Configure the payload with local IP address and local port number. Step 1 -Open your terminal.
Ii Configure the exploit with remote IP address and remote port number. TCP Scanner ports 1-65535 2. Iii Pick a payload.
Personal home-based networks wired and wireless including network reconnaissance and device inventorying. Ontdek zwakke plekken in de beveiliging van uw website applicatie of instrastructuur. Gathering intelligence eg network and domain names mail server to better understand how a target works and its potential vulnerabilities.
OpenVAS TCP Full Scan ports 1-65535 4. Action Pack any cyber security team can deploy their. Sudo apt-get install kali-linux-wireless your driver.
A targeted pentest is one of the best ways to ensure all network compliance requirements are being met. MELBOURNE Australia July 12 2022 GLOBE NEWSWIRE AttackForge a global leader in Pentest Management solutions has announced today AttackForge Core. Ontdek zwakke plekken in de beveiliging van uw website applicatie of instrastructuur.
OpenVAS UDP Full Scan top 1000 5. Disable the Windows Firewall. You can create a clone by Right clicking on the Virtul machine instance in VBox and click on clone You will notice that a cloned virtual WinXP will be created for you.
Nessus vulnerability scanning tool used for vulnerability assessment VA process Nmap network discovery and security auditing tool NetCat port scanning and listening tool used to read and write in a network. Defining the scope and goals of a test including the systems to be addressed and the testing methods to be used. The aim at this stage is not to simulate an attack on any vulnerabilities yet.
Network Pentest Checklist for Phase 2. Youd be amazed the ports you find open on that arent required providing an attack surface for potential threats. They may tell you that you have that one port open and perhaps identify the listening service on that port but you know that already.
When youre ready to start include the following tools in your scan template with the configuration below. Action Pack the worlds first on-demand dedicated tenant pentest management platform. With the launch of AttackForge Core.
This is easily done. Theres a home edition of Nessus. While youre examining your network traffic you should look for Link-Local Multicast Name Resolution LLMNR and ensure that its disabled if possible.
A very easy starting point would be to check open ports on all internet facing infrastructure. Ii Configure the exploit with remote IP address and remote port number. I Pick which exploit to use.
UDP Scanner top 1000 ports 3. Open ports are the key way for malicious hackers to gain unauthorized or backdoor access into a network and install malicious scripts. To connect the network you must type the username and click connect.
The weak points of a system are exploited in this process through an authorized simulated attack. TCP Scanner ports 1-65535 2. OpenVAS TCP Light Scan ports 1-65535 based on Nmap Vulnerability Scan.
Expect to find only the ports you know you have explicitly opened open. To connect the network you must type the username and click connect. Penetration Testing is the process of identifying security vulnerabilities in an application by evaluating the system or network with various malicious techniques.
Step 2 -Open the iwconfig step 4 -Open wlan0 in steps 5 and Dont make any changes if the problem isnt broken. To do this open a port on your router and rerun the scan. By clicking the network icon and holding down the WiFi adapters switch a WiFi network can be chosen to connect to.
CNAME Makes the domain name to another domain name. First of all you can try to get a technical friend to help. Just run and go.
Planning and reconnaissance The first stage involves. If you dont know any such person then grab a trusted friend who is non-technical and ask them to run a couple of small tests on your system. Creating a clone of it will prevent you from re-installing it again and again.
OpenVAS TCP Full Scan ports 1-65535 4. UDP Scanner top 1000 ports 3. Then verify that it is your home router that is performing the filtering and not your ISP.
But if you try to find out vulnerabilities in devices present in the test network then you should arrange some pen testing tool on your test network. This step is very helpful in case your VM gets corrupt. Once you connect to this network using your phone or computer you navigate to the router-page at 19216841 and input your credentials to your actual WiFi network.
The first thing they are going to do is port scan your IP address and find out what youve got running if anything. First have them try to get on your. However should you want to pentest these areas you would need to obtain explicit permission from the end user to inventory classify and perform a risk analysis on the networks supporting their.
You should not break it if you cant fix it. Ad Een pentest geeft u inzicht in de beveiligingsrisicos van uw bedrijf. The purpose of this test is to secure important data from outsiders like hackers who.
Expect everything else to be filtered. Here are a few security tools you can use to conduct pentesting for your network systems. OpenVAS UDP Full Scan top 1000 5.
Rarely are these part of a pentesting scope. Then verify that it is your home router that is performing the filtering and not your ISP. The first thing they are going to do is port scan your IP address and find out what youve got running if anything.
Disable the Windows Firewall. Once you do this your Lovebox will turn off the newly created WiFi network and connect to your actual WiFi. Threat modelling After collecting all the information you can about your target network its time to use this information for something dicey.
If youre not running anything and all ports are closed the attack is basically done unless there is a super critical known vulnerability unpatched on your edge router the chances of getting in with no ports open is extremely low. UDP Scanner top 1000 ports 3. Ad Een pentest geeft u inzicht in de beveiligingsrisicos van uw bedrijf.

7 Best Network Penetration Testing Tools In 2022 Demos Pros Cons
Building A Test Lab For Pentesting Guide White Oak Security

Wifi Pumpkin V0 8 7 Framework For Rogue Wi Fi Access Point Attack Computer Security Computer Technology Wifi Gadgets
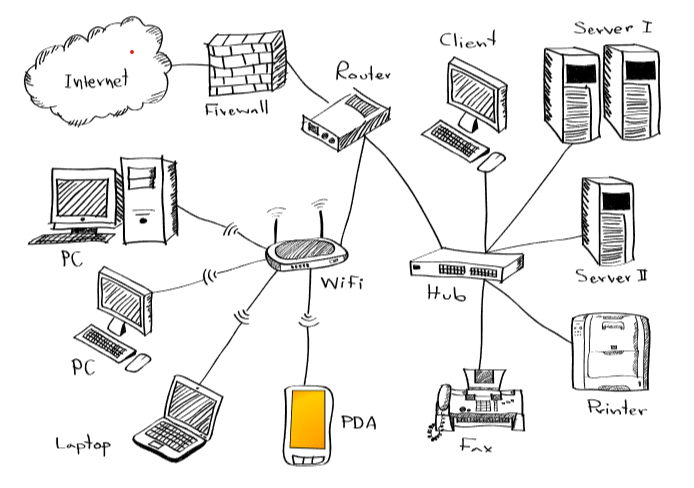
Enhance Your Home Wireless Network Security I Ironhack Blog
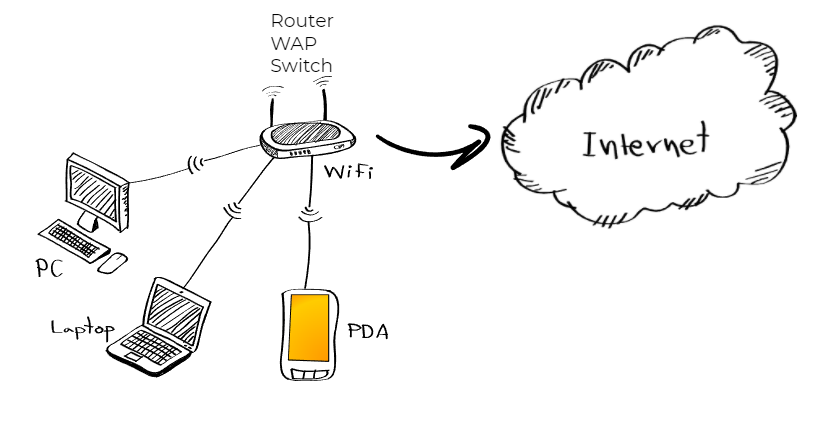
Enhance Your Home Wireless Network Security I Ironhack Blog

I Performed A Penetration Test On My Home Network

How To Scope A Network Penetration Test Pentester Tips Cobalt


0 comments
Post a Comment